6 minutes
The Unknown Browser Extension

We make use of browser extensions almost every day. It helps us in a variety of ways. Improving productivity, user experience, and the list goes on. It is more than a simple Icon sitting on the top right corner of the browser bar. If you don’t know what a browser extension is, read the description below.
A browser extension is a small software application that adds a capacity or functionality to a web browser. A browser extension, also called a plug-in, can take advantage of the same application program interfaces (APIs) that JavaScript can on a web page, but the extension can do more because it also has access to its own set of APIs.
Now I hope you have an idea of what a browser extension is. Being a security enthusiast myself I always wondered what could have gone wrong using these extensions. I have more than five extensions installed on my web browser. These extensions include cookie editors, web application technology identifier, grammar checker,…etc.
These extensions are very helpful and a time saver. Imagine you are a content writer, having a grammar checker on your browser will be super helpful when you want the sentences to look good. I have this browser extension which always helps me in writing good reports and emails. Let’s call the extension the “good ext”.
So what the good ext does is that as I write it will give suggestions and highlight which portions need changes. Cool right? but wait

Let us first understand what is happening here. To highlight those fields or to make those changes, the extension should interact with the DOM or simply it is interacting with the webpage that is loaded in the browser. It is injecting or adding elements to the webpage to make those changes.
You might be wondering what is wrong with this behavior. There is nothing wrong with this behavior until the good ext becomes the bad ext. There is no guarantee that an extension will only perform those actions which are put in its description. Imagine my cookie editor sending the web site cookies to a malicious server in the background. If so it could lead to the compromise of my online accounts, sensitive information, and other data. Nowadays we could add custom made extensions also.
In chrome, you could enable developer mode to load custom made extensions to your browser.
There are so many extensions available in Github itself. Which are useful for many purposes. After having all this information and doubts I did a small research on the same. Just to see what could have gone wrong if I install malicious extensions on my browser. I saw so many articles, various extensions in Github, videos, and also threatpost news. Researchers were warning users about malicious extensions for a very long time but the sad truth is nobody really cares about it. As long as it serves a purpose people are blindly installing these.

We have a lot of people around us who don’t know much about the extensions but use the extensions for daily needs. If something malicious can be done then it should be demoed also. For that, I made three custom chrome extensions. Namely,
- Krypton
- Carbon
- Log My Data
Krypton:- Simple web redirector. If you visit website A and you have krypton installed then you will automatically get redirected to website B.
Carbon:- For enabling Dark theme on your browser.
Log My Data:- For logging and analyzing data you have entered online.
Now that we have the extensions let’s see what could have gone wrong if the above three were malicious extensions.

Let’s start with Krypton. Imagine that someone or myself installed this extension on my browser. I won’t notice any quick changes in the look or feel of the browser. But the extension is actively listening for some event or the user to visit a particular URL. In this case, I set it to facebook.com. So when I visit facebook.com from my browser I will automatically get redirected to some other page. Now you might be getting some idea about what could go wrong here. Yes, it is similar to a phishing attack where the user is tricked to visit a page or do some action but in this case, you don’t have to worry about delivering any emails. It is more effective than a normal phishing attack where the user might become suspicious upon seeing the URL. In this case, the user enters a valid URL or domain name which in this case is facebook.com, and only upon loading the legitimate site it is getting redirected. If I have a clone of Facebook where I record every input field values I could have redirected the user to my site and steal their data. The user won’t notice these changes because initially he entered a valid URL and he will expect the rest of the pages from Facebook itself.
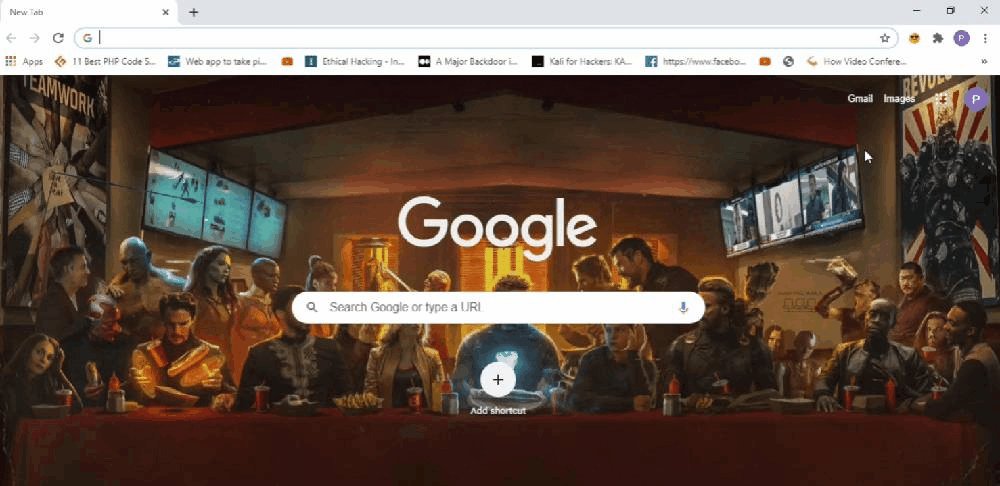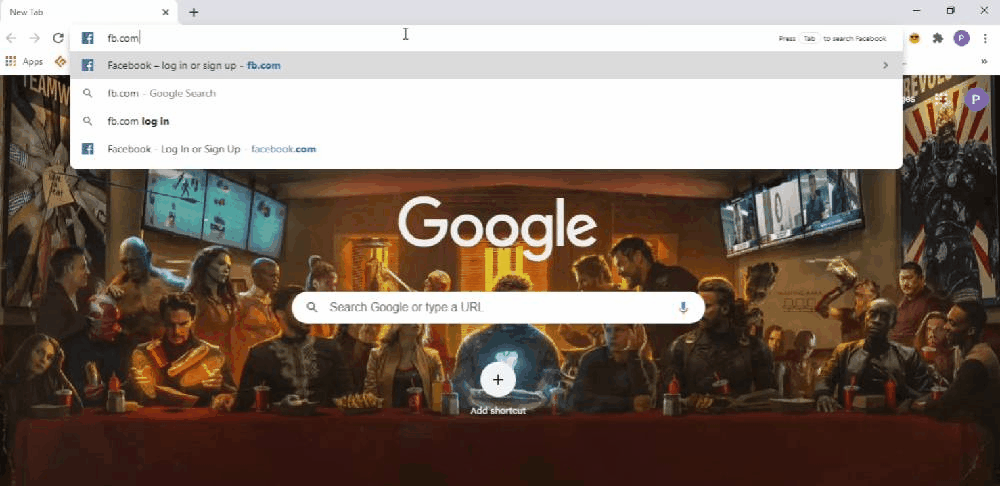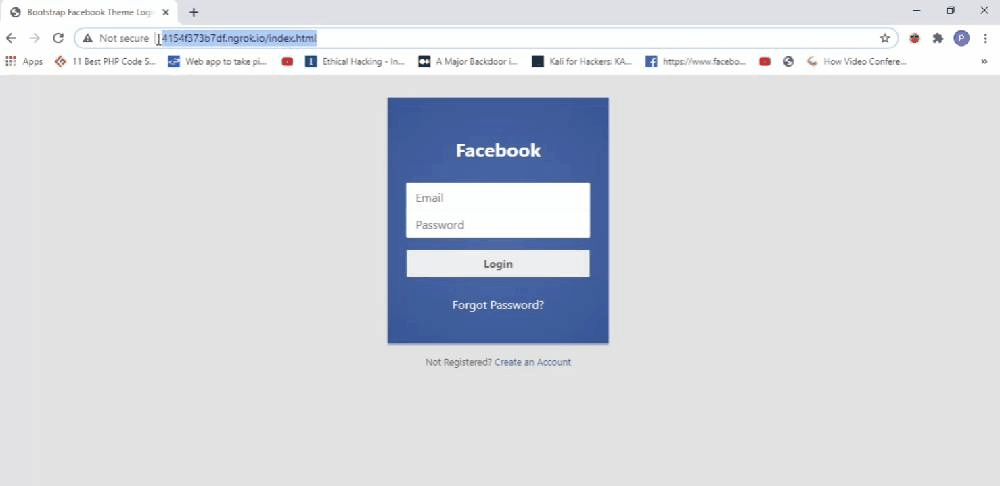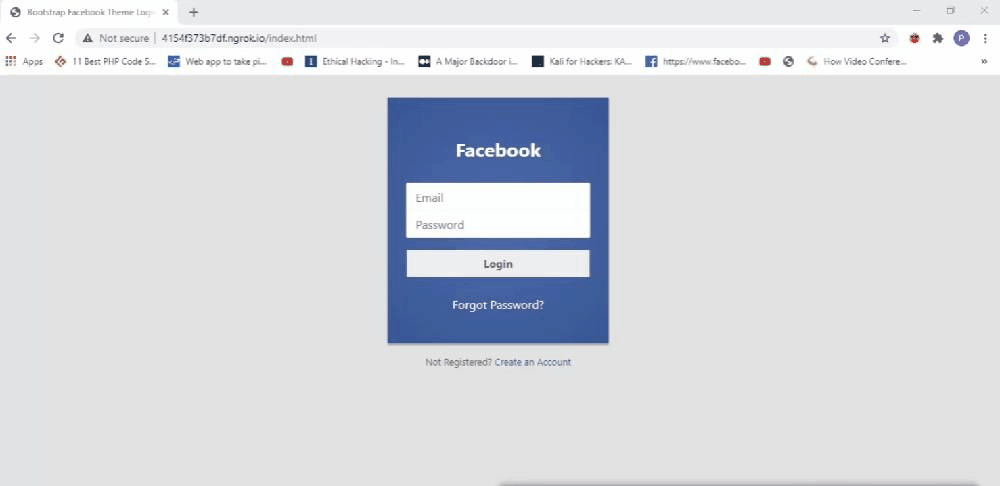
You might be on the attackers page even if the URL seems to be legitimate. Because what you see is limited to the browser you use. If the browser is vulnerable to address bar spoofing even an expert will be exposed to phishing attacks.
Let’s skip carbon because it is for integration purposes. Nobody will install a redirector extension because it is useless and annoying at the same time(Can only be used to prank). We could combine both Krypton and carbon to a single extension so that for the end-user it will be a dark mode enabler but in the background, it will do the actions as done by krypton.
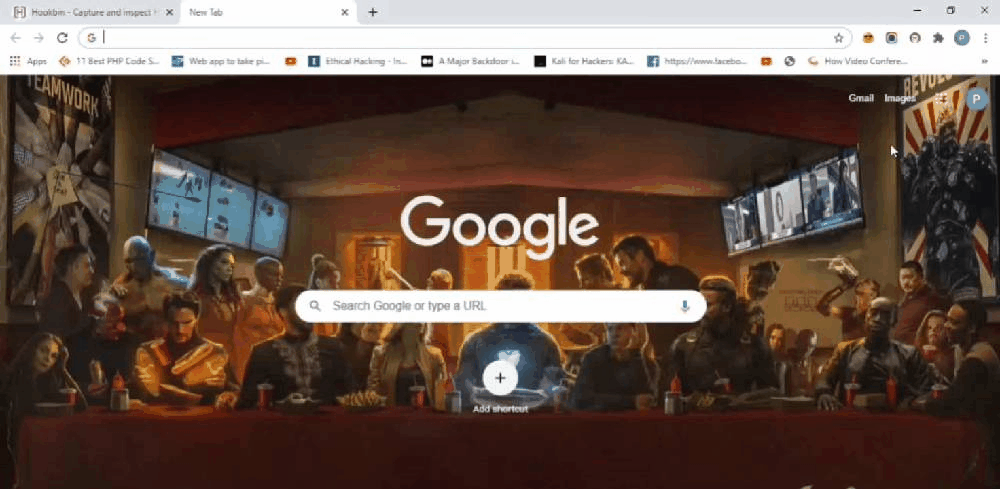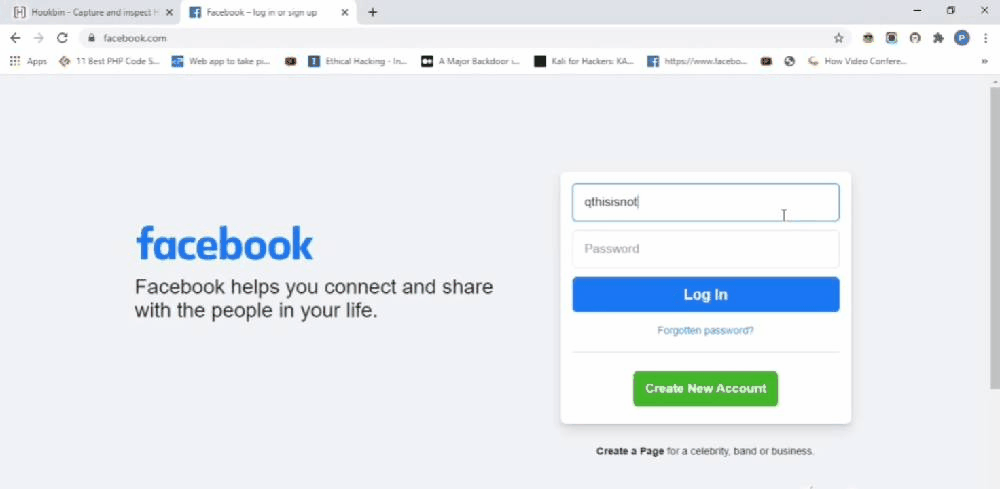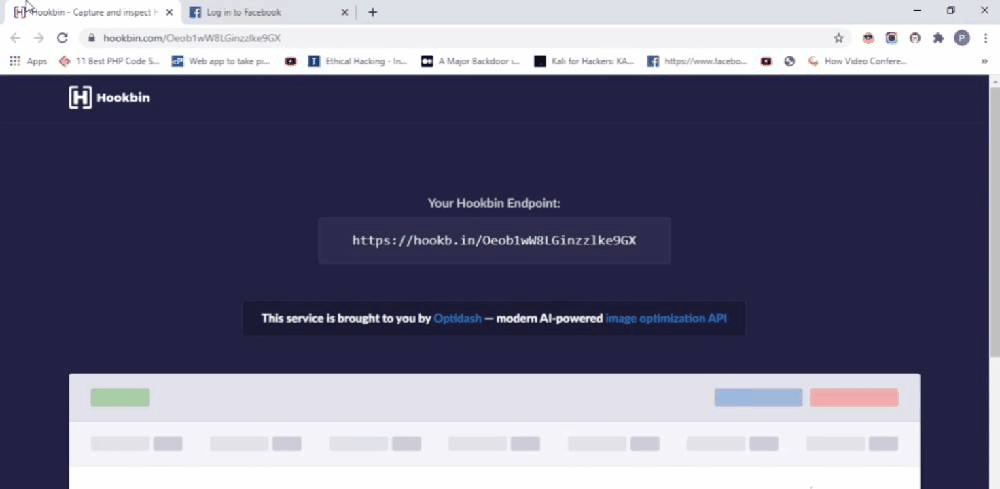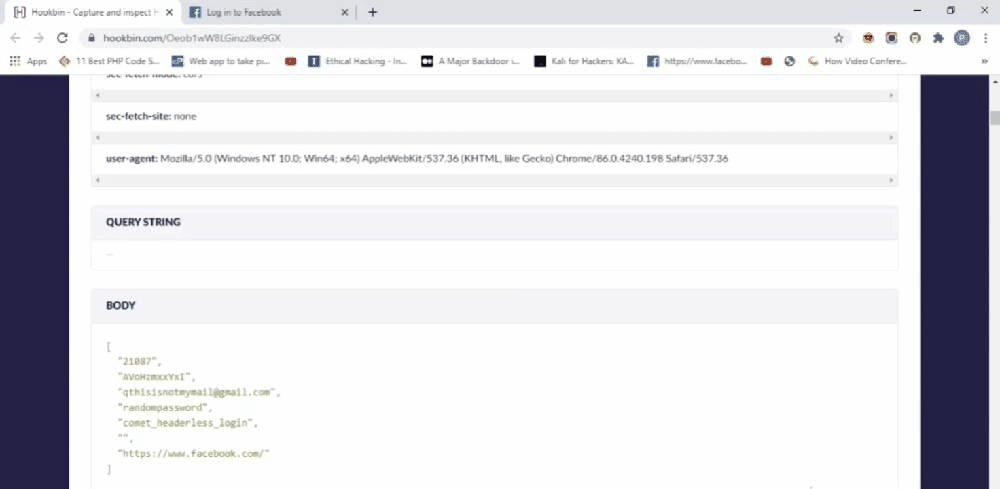
Now let us talk about Log my data(LMD). Of the three, the most interesting is LMD. This will help you monitor the data you have entered online and to store things that you may have forgotten. It stores information on the browser’s local storage. Local storage is a type of web storage that allows JavaScript sites and apps to store and access data right in the browser with no expiration date. This means the data stored in the browser will persist even after the browser window has been closed. It’s not a problem if the data is stored locally but it’s a problem if the data is sent to a server controlled by someone else. What if the extension stores the data locally and sent to a server at the same time. This is exactly what LMD does. It stores data in the browser and sends data to a server I control. LMD is capable of recording passwords, contact field information, mail id’s, form inputs,….etc. If someone installs LMD on their browser then every time they submit a form or log in to a site I will get a hit on my server with the data they’ve entered. I can also track which site the user is currently on.
💡 How to protect yourself from such extensions
- Install extensions from verified sources.
- If possible always use incognito mode for browsing. Extensions won’t work in this mode.
- Keep an eye on the permissions they have. In chrome click on the extension icon and go through the extension list. Analyze the permissions.
- Never use extensions from unknown sources or suggested by someone else.
- If you are installing an open-source browser extension, it is best to read the source code and understand the logic.